Live and deleted text messages are the most popular form of cell phone evidence recovered and admitted in civil and criminal cases today. Text message forensics is the science of recovering the evidence they hold for admission into the court record for adjudication of disputes. Live and deleted text messages consist of Short Message Service (SMS) messages and Multimedia Messaging Service (MMS) messages found on iPhones and Android smartphones. They also consist of proprietary iMessages on Apple’s iPhones and iPads.
Rounding out the mix are over one hundred alternative or specialty mobile messaging apps in use worldwide today. WhatsApp is the most popular messaging app and has a broad international market share. But Facebook Messenger, Snapchat, WeChat, and secure messaging apps like Telegram and Signal are a few of many mobile messaging apps to choose from while shopping from Apple’s App Store and Google’s Play Store. Forensic experts can recover deleted text messages from these various mobile apps.
Deleted Text Messages Forensic Recovery
Cell phone forensic experts spend perhaps 50% of their time trying to recover deleted text messages. Text messages comprise unique, fact-specific evidence that answers the what and when questions in legal disputes in which detailed statements or admissions are required. Enforcement of Orders for Protection (OFP) and Harassment Restraining Orders (HRO) are good examples of excellent matches between the need for relevant text messages to litigate disputes.
The text message expert’s analysis is guided by the lawyer’s goal of the examination. The goal is usually designed to recover and describe live and deleted text message evidence that may support the lawyer’s theory of the case.
Message Metadata Like Date Stamps and Read Status
Important metadata provides the foundation for text message evidence. For instance, the deleted text message status indicates whether the phone user deleted it from the smartphone. The message’s read status indicates whether the user opened and read the message. Some messages, like iPhone iMessages, have read receipt metadata, which when enabled in iPhone settings, record when the correspondent reads the iMessage.
Each text message identifies phone numbers to and from the smartphone, often with a user’s name matching the phone number taken from the phone contacts list. Date and time stamps show when the text message was sent, received, and read.
Text Message Reports
After deleted text message forensics analysis the expert will use his or her mobile device forensic tools to generate mobile evidence reports with responsive messages that satisfy the lawyer’s goal of the examination.
For instance, one mobile evidence report might be a chronology of text messages sent between the phone user and an important correspondent. The report will highlight text message content, including emojis and descriptive metadata like date and time stamps. Often, the report is presented in the courtroom by an expert witness in a colorful conversation or thread of messages that resemble the dialogs that may be seen on the smartphone’s screen.
The choice of form of production for text message reports includes options like Adobe PDFs and Microsoft Excel spreadsheets. Innovative and highly usable web browser reports are available, which support links to attachments and other helpful information. Lawyers and paralegals can view browser reports at no charge using Google Chrome, Microsoft Edge, Apple Safari, and Mozilla Firefox.
Portable case files are a new form of production with many advantages for the legal team. They provide mobile evidence but also no-cost forensic software which enables you to review it in your office on your computer. You can also search, filter, bookmark, and generate mobile reports using the forensic software designed for lawyers and investigators.
Many experts now send mobile evidence digitally from the forensics lab over the Internet for fast turnaround. Attorneys and paralegals can download it right away in their offices and start reviewing it immediately.
Deleted Text Messages are Essential Evidence
Carney Forensics has been recovering live and deleted text messages, calls, photos, videos, etc., from smartphones, feature phones, burners, and tablets for lawyers nationwide for fifteen years. For deleted text messages, we take a deeply probative extraction and decode the device with two or three tools to get a better shot at recovering the crucial evidence needed for your civil or criminal defense case.
We also examine over 902 unique mobile apps (WhatsApp, Snapchat, Kik, Telegram, Signal, TigerText, Facebook, etc.) to recover messages and other evidence. We filter deleted text messages by the phone number of the phone user’s correspondents to generate reports for your review. We also produce a timeline to clarify chronologically the text message evidence and the story it must tell.
The timing of collecting messages from smartphones is essential. The time between deleting a message and extracting the phone for its recovery is a critical factor. Deleted text messages are fragile and must be preserved at the earliest opportunity. Precarious, deleted text messages stored in the smartphone’s memory can be wiped by the operating system because of day-to-day usage and, therefore, may become unrecoverable.
Recovering deleted text messages from a smartphone can be tricky. The memory capacity available on the device to store mobile evidence directly affects the successful recovery. Text messages are small. After one or more of them are deleted, they can be overwritten by other data arriving over the air through 4G LTE, 5G, or nearby through Wi-Fi or Bluetooth. Photos and videos captured by the phone user are large and, when stored in the phone’s gallery, can wipe out hundreds, even thousands, of deleted text messages.
Encrypted Secure Messages
Using our text message forensics service, Carney Forensics recovers evidence in secure messaging apps, especially encrypted ones like WhatsApp, Telegram, and Signal. We locate and recover messaging app encryption keys and support decryption algorithms to expose them for production in civil and criminal cases.
Spoofed Text Messages
Many “spoofing” apps or services exist for sending anonymous messages and making anonymous calls on iOS and Android smartphones. Other legitimate apps offer a virtual or private phone number (not the device phone number) that enables users to text and place calls confidentially on a smartphone. Some legitimate apps offer complaint or gripe services, but spoofing apps generally do not provide them and do not operate in good faith.
Identifying the caller or texter, the harasser, depends on which app or service was used and how much metadata is available from a phone examination. Sometimes, text message experts can use the originating phone number, if available, to identify the service and the country or region of origin. Sometimes, the origin is an email address, which is of little value unless the domain identified the service. A subpoena is not actionable against the service unless the case is filed in court. Most often an investigation has not progressed that far to discover the suspect behind the unidentified spoofing.
Often, the harassed person has a good idea of the harasser’s identity, which might make a private investigation worthwhile. Some agencies have retired three letter agency talent on board that can sometimes shed light on the situation.
Retrieving Documents and Media from Text Messages
It appears document retrieval from messaging apps is more “art” than science for many legal practitioners in 2024. Many paralegals report difficulties recovering documents, photographs, and other attachments from live and deleted text message apps on iPhones and Android smartphones today, as well as tablets, including iPads, Amazon Fires, and Samsung tablets. They lack a viable process capable of producing repeatable and defensible results.
Paralegals mastered document recovery from emails decades ago. However, recovering documents from modern mobile messaging platforms is a new challenge that eludes much of the legal profession. A paralegal will usually start from scratch to discover messages for each case or each client. They use ad hoc or case-specific methods, which often disappoint and produce only screenshots or worse. Ultimately, parties are frustrated and the bench faces admissibility challenges due to unsound recovery or collection of messages with no authentication. We are looking for a better retrieval method that is reliable, repeatable, and forensically sound. Text message forensics encompasses methods and tools that can lead the way.
So, what types of live and deleted text messages do you encounter in your cases at law that must be retrieved? The vast majority are ordinary SMS text messages. SMS text messages with attachments are called MMS, which stands for multimedia messaging system. They are sent through the switches and cell towers of telecommunication carriers, or cell phone service providers like Verizon, AT&T, and T-Mobile.
Mobile messaging apps on smartphones also send and receive messages through the Internet instead of carrier switches and cell towers. These include Apple’s iMessage and third-party apps like Facebook Messenger, Snapchat, and many others.
So, what types of attached documents do you encounter in your cases at law that must be retrieved? Traditional Microsoft Office documents? What about Apple’s and Google’s documents? And Adobe Portable Document Formats, PDFs?
And what about the popular photographs and videos you find attached to messages on your smartphone? These are multimedia, but they can also include audio clips and recordings.
What about more unfamiliar document types you may find attached to messages on a cell phone? We often see voice messages, contacts, web links, and GPS geolocations attached to messages. These rare attachments are becoming popular, especially web links to articles and posts. GPS locations are often connected to messages to show where the other person is to be found.
The bottom line is that documents are anything attached to messages—just like documents attached to emails. Traditional documents are the ones lawyers think of as documents.
Demonstrative Exhibits from Messages with Documents and Media
Let’s consider credible demonstrative exhibits of document evidence competently retrieved from modern mobile messaging platforms to help you visualize successful outcomes. The exhibits that follow are from professional examinations of iPhones and Android smartphones.
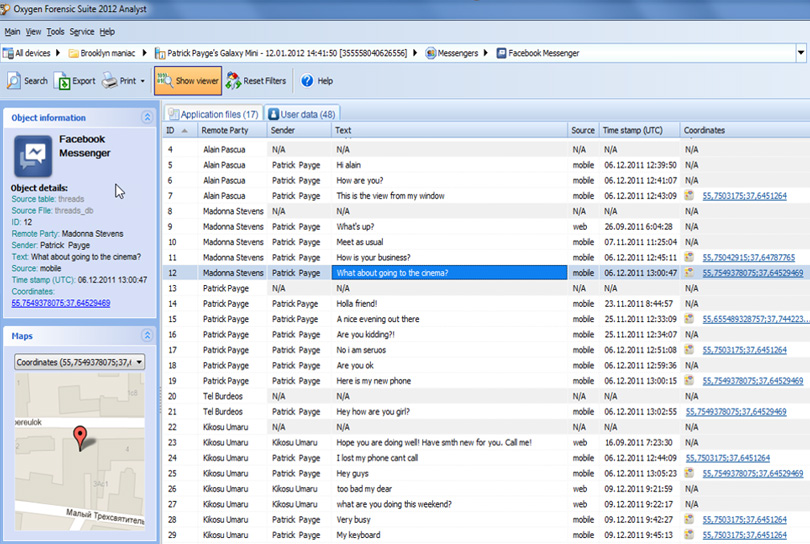
This first demonstrative exhibit below shows Facebook Messenger messages from an Android phone in the mobile device forensic tool. The messages are depicted in rows with content and metadata. The column on the right labeled Coordinates shows each message’s GPS location’s latitude and longitude.
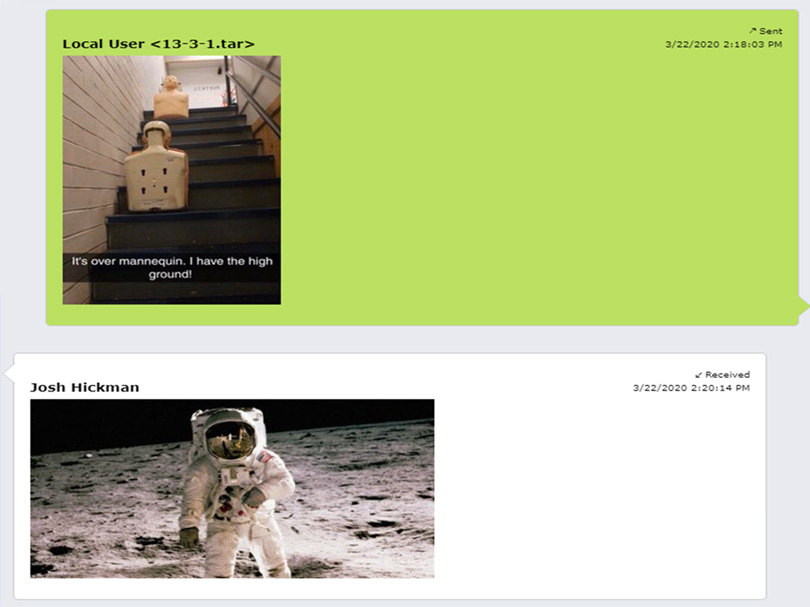
Below you see a Kik Messenger report showing a conversation with an exchange of attached photographs.
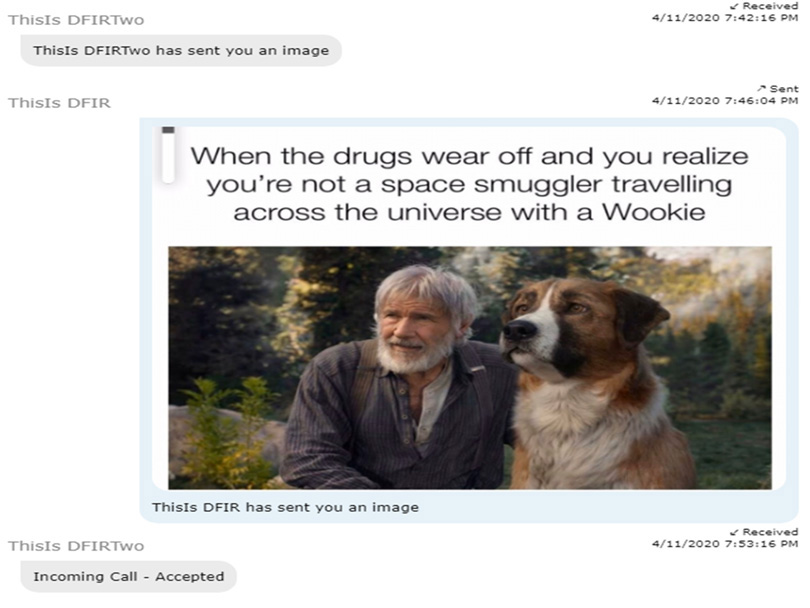
In this last demonstrative exhibit below, you see a mobile device forensic report from a Zoom meeting. It was held on a mobile phone, and the attendees were typing into the chat box. One of them attached this photograph or screenshot. Cell phone forensic experts can recover Zoom evidence, including chat box messages and attachments like this one.
Other Messaging and Document Evidence Sources
When mobile devices are lost or unavailable, what other message and document sources can be probed to recover deleted text messages?
Cell phone service providers or carriers like Verizon, AT&T, and T-Mobile provide ordinary text message logs in response to a subpoena or search warrant. They provide a phone number and a date and time stamp. But the logs do not include message content, the “text” in text messages. Carrier logs do not include documents or photographs attached to messages, as described above.
So text message experts at Carney Forensics check online, cloud sources for messages. They may not be recoverable from a cell phone but may still be available for forensic collection from connected accounts like Google, iCloud, and Samsung. We may also check other online accounts like Facebook and Snapchat for messages.